Digital Signatures
Description: Step through the digital signature process.
Key Words: digital, signature, electronic, encrypt, decrypt, hash, verify, key, pki, integrity
Level: High School Community College
Key Words: digital, signature, electronic, encrypt, decrypt, hash, verify, key, pki, integrity
Level: High School Community College
CryptoMatch
Description: Match the terms from the Cryptography Emate.
Key Words: cryptography, game, activity, match
Level: Community College University
Key Words: cryptography, game, activity, match
Level: Community College University
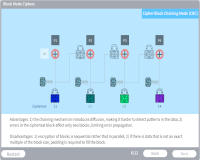
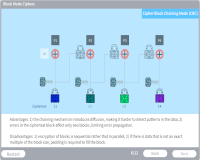
Block Mode
Description: Explore the five different Block Modes used in symmetric encryption algorithms.
Key Words: block, electronic codebook, mode, counter, cipher feedback, output feedback, ECB, CTR, CFB, OFB, cipher block chaining, CBC
Level: Community College University
Key Words: block, electronic codebook, mode, counter, cipher feedback, output feedback, ECB, CTR, CFB, OFB, cipher block chaining, CBC
Level: Community College University
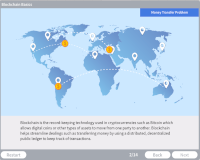
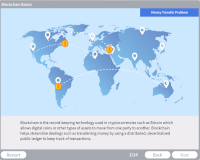
Blockchain
Description: Explore the record-keeping technology used in cryptocurrencies such as Bitcoin which allows digital coins or other types of assets to move from one party to another.
Key Words: bitcoin, crypto, ledger, hash, miner, blockchain
Level: High School Community College
Key Words: bitcoin, crypto, ledger, hash, miner, blockchain
Level: High School Community College
Cryptocurrency
Description: Explore the various forms of cryptocurrency and its application within several disciplines.
Key Words: ledger, block, chain, crypto, wallet, key, vulnerability
Level: High School Community College
Key Words: ledger, block, chain, crypto, wallet, key, vulnerability
Level: High School Community College
Cryptography
Description: Explore symmetric and asymmetric encryption methods along with digital signatures.
Key Words: symmetric, asymmetric, digital signature, algorithm, key, encrypt, decrypt, ciphertext, authentication, confidentiality, nonrepudiation, key, algorithm, strength
Level: High School Community College
Key Words: symmetric, asymmetric, digital signature, algorithm, key, encrypt, decrypt, ciphertext, authentication, confidentiality, nonrepudiation, key, algorithm, strength
Level: High School Community College
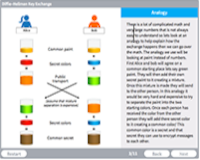
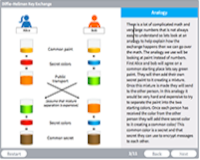
Diffie-Hellman Key Exchange
Description: Explore how the Diffie-Hellman Key exchange creates a secure communication method.
Key Words: trust, public, encrypt, decrypt, ciphertext, mod, key, exchange, prime number, exchange
Level: Community College University
Key Words: trust, public, encrypt, decrypt, ciphertext, mod, key, exchange, prime number, exchange
Level: Community College University
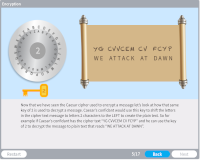
Encryption
Description: Explore how encryption provides data confidentiality.
Key Words: symmetric, asymmetric, ssl, algorithm, key, encrypt, decrypt, ciphertext, authentication, confidentiality, nonrepudiation
Level: Middle School High School Community College
Key Words: symmetric, asymmetric, ssl, algorithm, key, encrypt, decrypt, ciphertext, authentication, confidentiality, nonrepudiation
Level: Middle School High School Community College
Encryption and Data Formatting
Description: Explore the XOR operation and how it is used in encryption.
Key Words: encrypt, xor, encrypt, ascii, binary, decimal, hexadecimal, Boolean, gate, key,
Level: High School Community College
Key Words: encrypt, xor, encrypt, ascii, binary, decimal, hexadecimal, Boolean, gate, key,
Level: High School Community College
Hashing
Description: Explore the process of converting an input of any length using a mathematical or logical function into a fixed-sized output called a hash value or hash digest.
Key Words: hash, algorithm, digest, input, Boolean, function, MD5, SHA256, integrity
Level: High School Community College
Key Words: hash, algorithm, digest, input, Boolean, function, MD5, SHA256, integrity
Level: High School Community College
Hashing with Narration
Description: A narrated version of the Hashing Emate.
Key Words: hash, algorithm, digest, input, Boolean, function, MD5, SHA256, integrity
Level: High School Community College
Key Words: hash, algorithm, digest, input, Boolean, function, MD5, SHA256, integrity
Level: High School Community College
Kerberos
Description: Description: Explore the network authentication protocol that uses encryption, Kerberos.
Key Words: hash, algorithm, digest, input, Boolean, function, MD5, SHA256, integrity
Level: High School Community College
Key Words: hash, algorithm, digest, input, Boolean, function, MD5, SHA256, integrity
Level: High School Community College
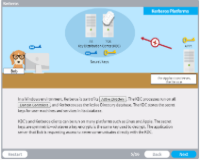
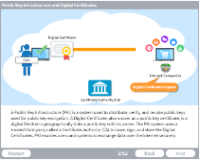
Public Key Infrastructure and Digital Certifications
Description: A Public Key Infrastructure (PKI) is a system used to distribute, verify, and revoke public keys used for public key encryption. A Digital Certificate, also known as a public key certificate, is a digital file that cryptographically links a public key with its owner and is part of the PKI system.
Key Words: public, key, pki, certificate, server, issue, hash, private, cryptography, trust, revoke, authentication, access, repudiation, integrity, confidentiality
Level: Community College University
Key Words: public, key, pki, certificate, server, issue, hash, private, cryptography, trust, revoke, authentication, access, repudiation, integrity, confidentiality
Level: Community College University
RSA Encryption
Description: Step through RSA key generation and the RSA algorithm for encryption and decryption.
Key Words: asymmetric, encryption, key, private, public, rsa, prime, factor, modulus, algorithm
Level: Community College University
Key Words: asymmetric, encryption, key, private, public, rsa, prime, factor, modulus, algorithm
Level: Community College University
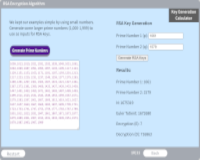
Factoring and Prime Numbers
Description: Factoring and prime numbers provide the foundation for cryptographic algorithms.
Key Words: prime, factor cryptography, key, composite, phi, totient, function, rsa
Level: Community College University
Key Words: prime, factor cryptography, key, composite, phi, totient, function, rsa
Level: Community College University