Career Exploration
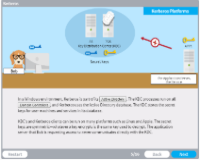
Description: Visit a security operations center with seven departments (investigate, securely provision, collect and operate, operate and maintain, protect and defend, analyze, oversee and governance) to discover the types of careers, credentials, and education and training required. The game creates a report card to track of all the flags you need to discover.
Key Words: cyber, cybersecurity, career, protect, defend, analyze, education, credential, operate, investigate, collect
Level: Middle School High School Community College
Key Words: cyber, cybersecurity, career, protect, defend, analyze, education, credential, operate, investigate, collect
Level: Middle School High School Community College
Cyber Hat Match
Description: Unscramble cybersecurity terms. Finish all eight (8) levels and you win. The game begins with 3-letter words. You get three attempts per term. Unscramble five terms at a level to move to the next level. Each subsequent level uses longer terms.
Key Words: game, cybersecurity, cyber, terms
Level: High School Community College
Key Words: game, cybersecurity, cyber, terms
Level: High School Community College
Cyber Scramble
Description: Unscramble cybersecurity terms. Finish all eight (8) levels and you win. The game begins with 3-letter words. You get three attempts per term. Unscramble five terms at a level to move to the next level. Each subsequent level uses longer terms.
Key Words: game, cybersecurity, cyber, terms
Level: Middle School High School Community College
Key Words: game, cybersecurity, cyber, terms
Level: Middle School High School Community College
Cybersecurity Scenario
Description: Discover the evidence before a hacker exploits the company's system.
Key Words: hack, easter, eggs, challenge, ctf, cyber
Level: Middle School High School
Key Words: hack, easter, eggs, challenge, ctf, cyber
Level: Middle School High School
Cookie Caper
Description: An interactive game to learn how cookies track information on a website.
Key Words: website, session, persistent, track, advertise, browsing, personal, information, attack, cookie, zombie, privacy, hijack
Level: Middle School High School Community College University
Key Words: website, session, persistent, track, advertise, browsing, personal, information, attack, cookie, zombie, privacy, hijack
Level: Middle School High School Community College University
Ethical Hacking Case
Description: Investigate a scene to find pieces of evidence and clues to a hacker's identity and solve the crime.
Key Words: reconnaissance footprint, investigate
Level: igh School Community College
Key Words: reconnaissance footprint, investigate
Level: igh School Community College
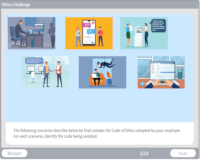
Ethics Challenge
Description: Investigate a scene to find pieces of evidence and clues to a hacker's identity and solve the crime.
Key Words: reconnaissance footprint, investigate
Level: High School Community College
Key Words: reconnaissance footprint, investigate
Level: High School Community College
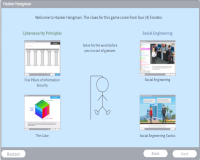
Hacker Hangman
Description: This game uses words (or clues) in two categories (cybersecurity principles and social engineering) from four Emates (Five Pillars of Information Security, The Cube, Social Engineering, and Social Engineering Tactics). Guess the word before the hacker hangs.
Key Words: game, cyber, principles, security
Level: Middle School High School Community College
Key Words: game, cyber, principles, security
Level: Middle School High School Community College
OSINT Personal Data Challenge
Description: Learn how to use open-source intelligence to provide a wealth of information.
Key Words: osint, public, intelligence, law, information, target, victim, metadata, location, dumpster, social, attack, tool
Level: Middle School High School Community College
Key Words: osint, public, intelligence, law, information, target, victim, metadata, location, dumpster, social, attack, tool
Level: Middle School High School Community College
Phishing Mystery
Description: Play along to see how phishing can capture useful information.
Key Words: attack, malicious, smish, vish, social, scam
Level: Middle School High School Community College
Key Words: attack, malicious, smish, vish, social, scam
Level: Middle School High School Community College
The Cube Challenge
Description: Assess the student’s understanding of the McCumber cube by classifying each challenge correctly by dimension--security principles, data states and countermeasures.
Key Words: mccumber, state, measure, property, confidentiality, integrity, availability, processing, storage, transmission, policy, technology, awareness, training, data, countermeasures, cybersecurity, principles, cube
Level: Community College University
Key Words: mccumber, state, measure, property, confidentiality, integrity, availability, processing, storage, transmission, policy, technology, awareness, training, data, countermeasures, cybersecurity, principles, cube
Level: Community College University
What’s My Crime?
Description: Match the social engineering technique with its description.
Key Words: phishing, baiting, whaling, dumpster diving, ransomware, pretexting, tailgating, shoulder surfing
Level: Middle School High School Community College
Key Words: phishing, baiting, whaling, dumpster diving, ransomware, pretexting, tailgating, shoulder surfing
Level: Middle School High School Community College
Various Types of Attacks Evaluation: Code Injection
Description: Assesses knowledge of the various code injection attacks.
Key Words: input, query, data, loss, sql, cross, code, command, injection, attack, secure, coding
Level: Middle School High School
Key Words: input, query, data, loss, sql, cross, code, command, injection, attack, secure, coding
Level: Middle School High School
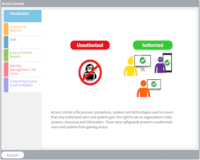
Access Control
Description: Explains the process, procedures, systems, and technologies used to ensure that only authorized users and systems gain the right to use data, systems, resources, and information.
Key Words: subject, object, model, identity, management, authorize, authentication, accountability, authorization, role, rule, dac, mac, access control, physical, logical, administrative
Level: Community College University
Key Words: subject, object, model, identity, management, authorize, authentication, accountability, authorization, role, rule, dac, mac, access control, physical, logical, administrative
Level: Community College University
Malware Types, Advanced Persistent Threats, Zero Day Attacks
Description: Malware (malicious code) is software that has been created for malicious or nefarious purposes. Malicious code can be installed in many devious ways that can be easy to miss by authorized users.
Key Words: virus, worm, trojan, access, logic bomb, keylogger, spyware, adware, bot, rootkit, threat, attack, zero-day
Level: Middle School High School Community College
Key Words: virus, worm, trojan, access, logic bomb, keylogger, spyware, adware, bot, rootkit, threat, attack, zero-day
Level: Middle School High School Community College
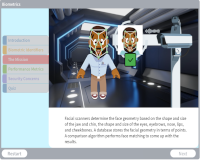
Biometrics
Description: Biometrics are body measurements and calculations based on unique physical characteristics and are used for authentication.
Key Words: authentication, recognition, retina, fingerprint, voice, hand, keystroke, signature, iris, physiological, behavioral, scan, metric, false error, rate, legal, ethical, biometric
Level: High School Community College
Key Words: authentication, recognition, retina, fingerprint, voice, hand, keystroke, signature, iris, physiological, behavioral, scan, metric, false error, rate, legal, ethical, biometric
Level: High School Community College
Buffer Overflow
Description: Programs allocate finite-sized blocks of memory, called buffers, to store data as they work on it. A buffer overflow happens when the amount of data written to or read from a buffer exceeds the capacity of what it can hold.
Key Words: block, memory, ram, code, attack, inject, malicious, overflow, buffer, attack, secure coding
Level: High School Community College
Key Words: block, memory, ram, code, attack, inject, malicious, overflow, buffer, attack, secure coding
Level: High School Community College
Code Injection Attacks
Description: illustrates how an attacker may insert an untrusted input into a program to achieve a malicious outcome
Key Words: input, query, data, loss, sql, cross, code, command, injection, attack, secure coding, buffer
Level: Middle School High School
Key Words: input, query, data, loss, sql, cross, code, command, injection, attack, secure coding, buffer
Level: Middle School High School
Configuration Management
Description: Configuration management identifies, controls, accounts for, and audits any changes made to an established baseline configuration.
Key Words: baseline, update, patch, antivirus, service, install, change, white, black, change control, configuration
Level: Community College University
Key Words: baseline, update, patch, antivirus, service, install, change, white, black, change control, configuration
Level: Community College University
Cross Site Scripting
Description: Discover how cross-site scripting is used to exploit web site vulnerabilities.
Key Words: code, inject, malicious, attack, web, browser, xss, javascript, input, secure coding
Level: High School Community College
Key Words: code, inject, malicious, attack, web, browser, xss, javascript, input, secure coding
Level: High School Community College
The Cube
Description: Explores a framework used to establish and evaluate information security.
Key Words: mccumber, state, measure, property, confidentiality, integrity, availability, processing, storage, transmission, policy, technology, awareness, training, data, countermeasures, cybersecurity, principles
Level: Middle School High School Community College University
Key Words: mccumber, state, measure, property, confidentiality, integrity, availability, processing, storage, transmission, policy, technology, awareness, training, data, countermeasures, cybersecurity, principles
Level: Middle School High School Community College University
Cybersecurity Controls
Description: Explore the various types of cybersecurity controls that an organization implements to avoid, detect, counteract, or minimize security risks to its assets.
Key Words: preventative, detective, corrective, deterrent, recovery, compensating, compliance, administrative, technical, physical, controls
Level: Community College University
Key Words: preventative, detective, corrective, deterrent, recovery, compensating, compliance, administrative, technical, physical, controls
Level: Community College University
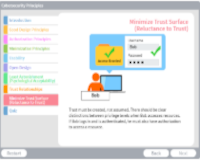
Cybersecurity Design Principles
Description: Explore how security design principles help to achieve the main tenets of information security.
Key Words: principle, authorization, minimization, usability, open, least, astonishment, trust, modularity, layering, separation, fail, isolation, design, cybersecurity
Level: Community College University
Key Words: principle, authorization, minimization, usability, open, least, astonishment, trust, modularity, layering, separation, fail, isolation, design, cybersecurity
Level: Community College University
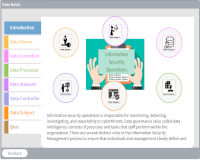
Data Roles
Description: Explore several distinct roles in the Information Security Management process to ensure that individuals and management clearly define and understand critical responsibilities in managing the organization’s information assets.
Key Words: owner, custodian, processor, steward, controller, subject, governance, threat, policy
Level: Community College University
Key Words: owner, custodian, processor, steward, controller, subject, governance, threat, policy
Level: Community College University
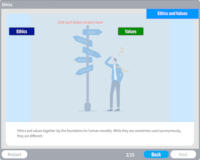
Ethics and Professional Conduct
Description: Explore ethics and values as they particularly apply to the code of ethics developed by the Computer Ethics Institute.
Key Words: value, rules, beliefs, code, spy, steal, property, pirate, unauthorized, ethics, constraint, motivation, consistency, morals
Level: High School Community College
Key Words: value, rules, beliefs, code, spy, steal, property, pirate, unauthorized, ethics, constraint, motivation, consistency, morals
Level: High School Community College
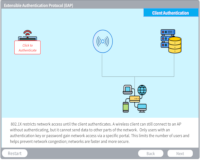
Extensible Authentication Protocol
Description: Extensible Authentication Protocol (EAP) in an authentication framework which provides a secure way to send identifying information for network authentication.
Key Words: 802, authentication, framework, leap, peap
Level: Community College University
Key Words: 802, authentication, framework, leap, peap
Level: Community College University
Firewalls
Description: Explore the function of a firewall and the various firewall technologies.
Key Words: rules, trust, network, host, traffic, stateless, packet, stateful, application, proxy, filter
Level: Community College University
Key Words: rules, trust, network, host, traffic, stateless, packet, stateful, application, proxy, filter
Level: Community College University
Five Pillars of Information Security
Description: Explore the examples and security components that support the five pillars of information security...confidentiality, integrity, availability, authenticity, and nonrepudiation.
Key Words: confidentiality, integrity, availability, authenticity, nonrepudiation, cia, authentication
Level: Middle School High School Community College
Key Words: confidentiality, integrity, availability, authenticity, nonrepudiation, cia, authentication
Level: Middle School High School Community College
Google Hacking
Description: Learn how easy it is to find valuable data and exploit it using Google.
Key Words: footprint, social, media, search, websites, vulnerable, pen, tester, phishing
Level: High School Community College
Key Words: footprint, social, media, search, websites, vulnerable, pen, tester, phishing
Level: High School Community College
Heartbleed Bug
Description: Learn how the heartbleed bug exploited vulnerabilities.
Key Words: vulnerability, ssl, tls, key, attack, eavesdrop, communication, code, attack
Level: High School Community College
Key Words: vulnerability, ssl, tls, key, attack, eavesdrop, communication, code, attack
Level: High School Community College
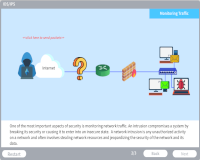
IDS/IPS
Description: Explore Intrusion detection systems (IDS) and intrusion prevention systems (IPS), tools used to monitor the network.
Key Words: intrusion detection system, intrusion prevention system, ids, ips, monitor, alert, packet, rules, unauthorized, signature, anomaly, behavior, sensors
Level: Community College University
Key Words: intrusion detection system, intrusion prevention system, ids, ips, monitor, alert, packet, rules, unauthorized, signature, anomaly, behavior, sensors
Level: Community College University
Kerberos
Description: Explore the network authentication protocol that uses encryption, Kerberos.
Key Words: authentication, protocol, network, encrypt, key, trust, server, domain, hash, three-headed dog
Level: Community College University
Key Words: authentication, protocol, network, encrypt, key, trust, server, domain, hash, three-headed dog
Level: Community College University
Meltdown and Spectre
Description: Explore how Meltdown and Spectre affect CPUs released since 1995.
Key Words: vulnerability, memory, exploit, attack, code, patch
Level: Middle School High School Community College University
Key Words: vulnerability, memory, exploit, attack, code, patch
Level: Middle School High School Community College University
NAT/PAT
Description: The use of NAT and PAT hides the real IP address of internal devices, allows multiple private addresses to access one Internet connection, and helps to conserve IP address space.
Key Words: address, port, translation, public, private, IP, class, default, gateway, router, network, multicast
Level: High School Community College
Key Words: address, port, translation, public, private, IP, class, default, gateway, router, network, multicast
Level: High School Community College
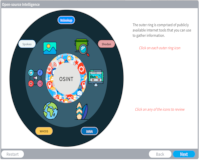
Open-Source Intelligence
Description: Explore the different sources available to collect data from public resources.
Key Words: osint, public, intelligence, law, information, target, victim, metadata, location, dumpster, social, attack, tool, open-source
Level: Middle School High School Community College
Key Words: osint, public, intelligence, law, information, target, victim, metadata, location, dumpster, social, attack, tool, open-source
Level: Middle School High School Community College
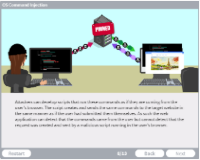
OS Command Injection
Description: Learn how attackers can exploit vulnerable web application by creating scripts that execute commands.
Key Words: attack, web, injection, headers, code, vulnerability, operating system, attack
Level: High School Community College
Key Words: attack, web, injection, headers, code, vulnerability, operating system, attack
Level: High School Community College
Pen Testing
Description: Learn how pen testing seeks to breach systems, people, processes, and code to uncover vulnerabilities.
Key Words: network, attack, scan, reconnaissance, access, analysis, exploit, enumeration, packet, policy, train, hacking, pen test, penetration testing
Level: Middle School High School Community College University
Key Words: network, attack, scan, reconnaissance, access, analysis, exploit, enumeration, packet, policy, train, hacking, pen test, penetration testing
Level: Middle School High School Community College University
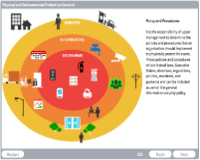
Physical and Environmental Protection Controls
Description: Physical and environmental security includes measures that protect systems, buildings and infrastructure against threats associated with the physical environment.
Key Words: perimeter, layer, infrastructure, building, access, policy, information, facility, power, location, site
Level: High School Community College
Key Words: perimeter, layer, infrastructure, building, access, policy, information, facility, power, location, site
Level: High School Community College
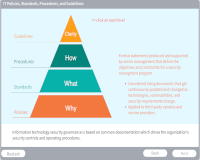
Policies, Standards, Procedures, and Guidelines
Description: Describes an organization's governance strategy based on the documents in place.
Key Words: governance, guideline, procedure, standard, policy, documentation, best practices, framework, compliance, roles, awareness
Level: High School Community College
Key Words: governance, guideline, procedure, standard, policy, documentation, best practices, framework, compliance, roles, awareness
Level: High School Community College
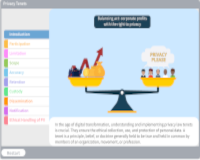
Privacy Tenets
Description: Understand privacy tenets, which ensure the ethical collection, use, and protection of personal data.
Key Words: privacy, law, participation, limitation, scope, accuracy, retention, custody, dissemination, notification, ethical, pii, personal, data
Level: High School Community College
Key Words: privacy, law, participation, limitation, scope, accuracy, retention, custody, dissemination, notification, ethical, pii, personal, data
Level: High School Community College
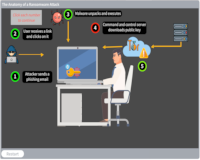
The Anatomy of a Ransomware Attack
Description: Proceed step by step through a ransomware attack.
Key Words: access, hack, ransom, payment, email, malware, public, key, encrypt, bitcoin, attack
Level: Middle School High School Community College
Key Words: access, hack, ransom, payment, email, malware, public, key, encrypt, bitcoin, attack
Level: Middle School High School Community College
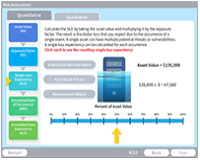
Risk Analysis
Description: A risk analysis determines possible vulnerabilities and threats, their likelihood and consequences, and the tolerances for such events.
Key Words: vulnerability, threat, quantitative, qualitative, asset, tangible, value, exposure, loss, annual rate, analysis, risk
Level: Community College University
Key Words: vulnerability, threat, quantitative, qualitative, asset, tangible, value, exposure, loss, annual rate, analysis, risk
Level: Community College University
Risk Management
Description: Risk management is a formal process that reduces the impact of threats and vulnerabilities.
Key Words: risk, analysis, monitor, respond, assess, due care, due diligence, negligence, asset, threat, agent, vulnerability, countermeasure, control, impact, exposure
Level: Community College University
Key Words: risk, analysis, monitor, respond, assess, due care, due diligence, negligence, asset, threat, agent, vulnerability, countermeasure, control, impact, exposure
Level: Community College University
Social Engineering
Description: Social engineering is a broad range of malicious activities accomplished through psychological manipulation of people into performing actions or divulging confidential information.
Key Words: attack, bait, shoulder surf, pretext, phish, spear, ransomware, tailgating, dumpster, mitigate
Level: Middle School High School Community College
Key Words: attack, bait, shoulder surf, pretext, phish, spear, ransomware, tailgating, dumpster, mitigate
Level: Middle School High School Community College
Social Engineering Psychological Tactics
Description: Explore how hackers use various tactics to persuade targets to provide information or take a specific action.
Key Words: tactic, target, reciprocity, scarcity, authority, consistency, liking, social proof, persuasion
Level: Middle School High School Community College
Key Words: tactic, target, reciprocity, scarcity, authority, consistency, liking, social proof, persuasion
Level: Middle School High School Community College
Spoofing Attacks
Description: Spoofing attacks occur when an attacker successfully masquerades as another by falsifying data to gain an illegitimate advantage resulting in stolen data, malware, or bypassed access controls.
Key Words: arp, dns, ip address, mac, network, dos, hijack, packet, host, tcp, exploit, attack, impersonation, spoofing
Level: High School Community College
Key Words: arp, dns, ip address, mac, network, dos, hijack, packet, host, tcp, exploit, attack, impersonation, spoofing
Level: High School Community College
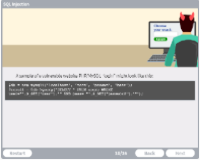
SQL Injection
Description: Learn how hackers use SQL injection to output data unintentionally.
Key Words: attack, database, web, query, exploit, vulnerable, code
Level: High School Community College
Key Words: attack, database, web, query, exploit, vulnerable, code
Level: High School Community College
Stuxnet
Description: Learn how Stuxnet, a sophisticated computer worm, exploited a Windows vulnerability to infect SCADA systems.
Key Words: worm, exploit, vulnerability, plc, rootkit
Level: Middle School High School Community College
Key Words: worm, exploit, vulnerability, plc, rootkit
Level: Middle School High School Community College
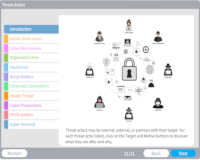
Threat Actors
Description: Learn the various types of threat agents and what motivates each.
Key Words: cyber, agent, hack, hat, state, crime, hacktivist, script kiddie, insider, thrill, terrorist, actor
Level: Middle School High School Community College
Key Words: cyber, agent, hack, hat, state, crime, hacktivist, script kiddie, insider, thrill, terrorist, actor
Level: Middle School High School Community College
Three-way Handshake, Denial of Service, Distributed Denial of Service
Description: Learn how the three-way handshake creates a connection between communicating computers.
Key Words: handshake, tcp, transmission, protocol, SYN, ACK, acknowledgement, DOS, denial of service, DDOS, distributed denial of service
Level: Middle School High School Community College University
Key Words: handshake, tcp, transmission, protocol, SYN, ACK, acknowledgement, DOS, denial of service, DDOS, distributed denial of service
Level: Middle School High School Community College University
Wireless Security
Description: Learn how wireless security has evolved over the years.
Key Words: ssid, encryption, key management, data integrity, authentication, key, WEP, WPA, TKIP, CCMP, EAP, protocol
Level: Community College
Key Words: ssid, encryption, key management, data integrity, authentication, key, WEP, WPA, TKIP, CCMP, EAP, protocol
Level: Community College
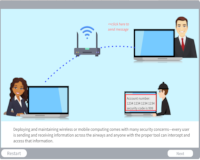
Virtual Private Networks
Description: Explore how a VPN can safeguard online activities and keep sensitive data secure.
Key Words: vpn, encrypt, public, network, tunnel, address, remote access, site-to-site, mobile, personal
Level: Community College
Key Words: vpn, encrypt, public, network, tunnel, address, remote access, site-to-site, mobile, personal
Level: Community College
Protocol Analysis
Description: Monitoring network protocols is crucial for identifying potential threats and ensuring the security of an organization's infrastructure.
Key Words: protocol, header, analysis, analyst, cyber, ip, tcp, udp, icmp, ntp, smtp, pop3, imap, email, http, ftp, web, data, packet, arp, threat, attack, malicious
Level: Community College
Key Words: protocol, header, analysis, analyst, cyber, ip, tcp, udp, icmp, ntp, smtp, pop3, imap, email, http, ftp, web, data, packet, arp, threat, attack, malicious
Level: Community College
Games/Activities
Instructional